Dualboot encrypted Windows and Ubuntu
Backgrounds to system encryption
What is encryption?
Encryption makes data unavailable for unauthorized individuals. If you have a laptop the data is normally written to your harddisk and can be read by anyone. Do you think nobody can access your files by activating a Windows password? Well, the password protects only in a way you can’t login into the desktop, but all your files are still on the disk in a readable way. The password can be completely bypassed through accessing your disk by another operating system started from another media and further investigate your disk from it.
So password protection doesn’t protect your files for others when they physically have access to your laptop or harddrive. That’s where encryption comes in. Because of the complexity about encryption I will explein only the very, very basics here. For more information use Wikipedia, Google, read a book or start an university course. Encryption converts readable data to unreadable data by using a secret key. When you have that secret key you can convert (decrypt) the unreadable data back to readable data. But when you don’t have the secret key, you can only access the unreadable data which looks like garbage. The secret key is based on a password or passphrase. What is the difference? A password is usually about 4 until 20 character long, depending on the application, and doesn’t usually contain spaces. A passphrase is intended to be very long like 100 characters. The goal for using a passphrase is to make it harder to guess or bruteforce the password.
There are multiple ways to encrypt files on a disk like file based encryption where only 1 datafile is encrypted, but I will focus on disk encryption. Disk encryption applies to a whole disk or partition. All information including metadata is encrypted. Temporary copy’s and directory structure are not accessible and therefore disk encryption is a safer solution than file based encryption in most cases. In case the encrypted disk contains an operating system, pre-boot authentication is used to access the disk before starting the operating system itself. And that’s where boot sectors come in.
Used encryption products
There’s a lot of software today to apply encryption to your system. I will focus only to open source disk encryption for Windows and Ubuntu.
Truecrypt is free open source encryption software available for Windows, Linux and Mac OS X. Truecrypt can create virtual disks within a file or can encrypt a whole partition or storage device like an USB stick. On Windows only, it can encrypt the system partition and use pre-boot authentication to protect the operating system. Truecrypt installs its own bootloader in the master boot record (MBR) to enable pre-boot authentication. More about the boot process later…
Ubuntu supports file system encryption with LUKS and dm-crypt. Both are open source software and available in most linux distributions bundled together as cryptsetup. Together they enable system encryption. dm-crypt is a device mapper which is used to access partitions, LUKS handles the key management. The pre-boot authentication doesn’t take place by code in the master boot record like Truecrypt does. Linux operating systems have a boot manager called Grub and a boot partition which contains the kernel and a initrd file. This initrd contains drivers, startup scripts and the crypto software which handles the authentication. When the correct password has entered the encrypted filesystem with all data on it can be mounted. So all the data is encrypted, except for the boot partition. That is not a problem because the boot partition contains only the ‘/boot’ directory and does not contain any user data. More detailed information about dm-crypt and LUKS can be found on the website owned by Markus Gattol.
Boot sectors, master boot record and volume boot record
Another bit of theory is about boot sectors, how do they work? A harddisk contains a master boot record (MBR) and one more partitions. The master boot record contains the code executed by the BIOS during the boot process. This code can handle the partition format and loads the operating system. The master boot record is located at the first 512 bytes of the harddrive. The MBR is also called a boot sector. A harddisk can actually contain multiple boot sectors. Each partition contains a boot sector, called the volume boot record. So on a harddrive basis, the master boot record only exists once, the volume boot record once per partition. They both are called boot sectors and can contain bootloaders.
About bootloaders
Why is that boot sector stuff that important? Well, both Windows as Linux need to start with a boot sector containing the bootcode for the OS. For Windows (if encrypted) it is the Truecrypt bootloader, for Linux it is the boot manager called Grub. If encryption isn’t the case then Grub has all capabilities to boot both Windows and Linux. With encryption enabled Windows really needs the Truecrypt pre-boot authentication, and Linux really needs the Grub loader while there’s only place for one boot loader in the MBR. How to solve this? Remember that a boot sector not necessarily need to be in the MBR, but can also be in the volume boot record in the partition. The Truecrypt bootloader must be installed in the MBR while grub can be installed in the volume boot record inside a partition. The trick is that Truecrypt has a multiboot option which enables the computer to chainload to a second bootloader in other available partitions. When using the multiboot option in the Truecrypt bootloader, the system tries to find other partitions to boot and will find the bootsector of the linux boot partition. The Truecrypt multiboot option must be enabled when configuring the system encryption in Truecrypt. To enter the multiboot function, you can use the escape button during the pre-boot authentication when the system asks for the Truecrypt password.
Use a minimum amount of partitions
When activating the Truecrypt multiboot function using the escape button, the boatloader looks for other partitions. If only one other bootable partition exists, the operating system on that partition will be started. If multiple other bootable partitions exists, then a bootmenu will show up containing all that partitions as option. The bootmenu which let you choose which partition to start can be annoying because of the fact that user interaction must be minimal during startup time. To accomplish that, Windows and Ubuntu must be installed in a way that the amount of partitions are minimal. Best is to install Windows in only one partition. For Ubuntu you can create a LVM volume within an encrypted volume. Inside that LVM you can create volumes for the root, swap and possibly other partitions. The Ubuntu boot partition is the only partition outside the LVM and is the only partition which isn’t encrypted.
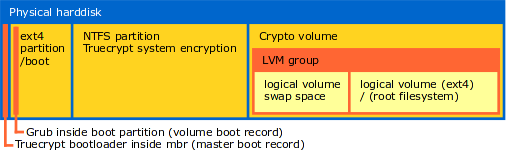
The picture above represents a harddisk. It contains three partitions. First is the boot partition for Ubuntu. This one is not encrypted but does not contain any data, except for the kernel, startup-scripts and drivers. The second partition is the NTFS partition for Windows, encrypted with Truecrypt. The third partitions represents a crypto volume. The crypto volume contains a LVM volume with two logical volumes. The first is the swap space, the second is the root filesystem, both for Ubuntu. All the data inside the crypto volume is encrypted. Swap space and the root filesystem are only available when authentication to the crypto volume was successful. There are two bootsectors in use. First is the Truecrypt bootloader in the master boot record. Second is Grub inside the volume boot record inside the boot partition for Ubuntu.
Avoiding the creation of the Windows 7 system partition
When partitioning the harddrive during the installation process, Windows 7 will create two NTFS partitions, one of them is a 100 MB system partition containing recovery files. That second partition is no problem but, as I mentioned before, can be annoying. There are 2 solutions to get rid of that system partition. The first and simplest solution is to delete that 100 MB partition directly after is created when you’re still in the installation mode. The 100 MB of released, unused space can be used for the Linux boot partition, however it is a bit small, or you accept that your harddisk doesn’t use that 100 MB. The second is to pre-partition your harddrive with only one NTFS partition and other (temporary) partition that fills up all the remaining space. If Windows 7 can’t create the 100 MB system partition it will place the files on the main partition. So you won’t loose any of the functionality offered by the system partition.

Leave a Reply